
Application Access Management (AAM): Authentication Offload Solution
The Need for Edge Authentication
Organizations typically run many Web and business applications—often including Oracle, SAP, and Exchange—according to their business needs. In many cases, these organizations must provide endusers and employees access to these applications over the Internet. This brings up a potential security concern for IT teams. Stringent network design and enhanced security policies are needed to provide secure access to these assets over the Internet.
Enterprises use authentication to protect network resources from unauthorized access. Authentication is used to determine whether access should be granted to each individual end-user. Sample use cases include:
- Public Web sites
- Access to sensitive applications such as online banking, shopping portals, stock trading web sites, and so on
- External access to internal assets, where a layer of authentication may not be needed internally
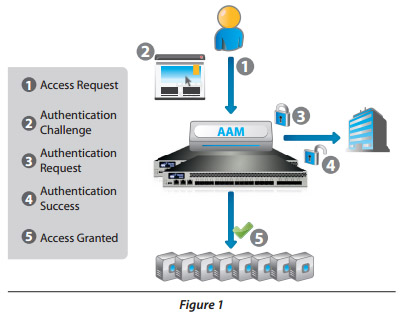
A10's Application Access Management (AAM) solution, available on the A10 Thunder Series and AX Series ADCs, is a set of services for optimizing and enforcing Authentication and Authorization for client-server traffic
Figure 1 shows how the AAM solution can be seamlessly integrated into your existing application infrastructure. The AAM provides enhanced protection and server efficiency by o oading authentication processing from AAA servers.
Authentication Offloa
Authentication processing adds overhead, and when multiple servers are involved, management complexity also increases. Authentication servers also can be vulnerable to attacks.
With A10's AAM solution, the A10 device acts as an edge authentication point for web services. A10 customers can o oad the burden of authentication processing to the A10 device, thereby increasing server e ciency and adding an extra layer of protection for web servers. AAM also o ers Online Certi cate Status Protocol (OCSP), which enables seamless sign-on for BYOD and similar devices using certificate based authentication.
The AAM solution provides centralized management of authentication for web servers. For example, an IT team can use AAM to require authentication to a previously internal-only wiki or Web site when accessed by external users. AAM serves as central authentication point for the external users. AAM eliminates the need to maintain separate authentication points on each Web server.
Optimization and Enhanced Security
Managing multiple authentication points for various application servers can be a daunting task and increases network complexity. Setting up a client authentication scheme for each application may require costly and time consuming custom development work. AAM provides centralized access policy management. Consolidation of multiple authentication points reduces interoperability and integration issues. The A10 device adds an extra layer of security by providing pre-authentication functionality for business-critical Web server applications (such as Oracle Financials). Pre-authentication enables secure access to internal systems without the need to change multiple con gurations in the existing infrastructure.
AAM also o ffers a Kerberos Single Sign-On (SSO) security solution that allows non-Kerberos end-users to access services protected by your Kerberos realm, with a single login. End-users do not need to log in again for subsequent requests until the session expires.
Basic HTTP Authentication
Basic HTTP authentication uses a simple HTTP request to challenge clients for their access credentials (typically, username and password). In detail:
- The end-user sends an HTTP access request to the server
- The A10 device sends an authentication challenge (WWWauthenticate header) to the end-user for basic authentication
- The end-user's browser launches a login screen, requesting username and password. Once complete, the browser sends a request containing the user credentials to the A10 device. The A10 device, transparently to the end-user, forwards the credentials to the authentication server for veri cation
- If authentication is successful, the authentication server sends a success message to the A10 device
- The A10 device grants the end-user access to the requested application
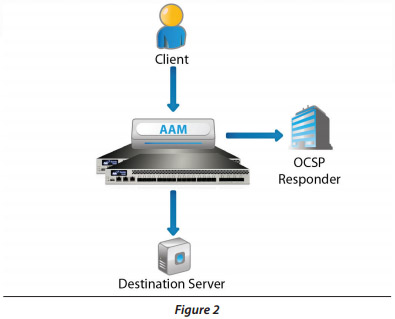
Online Certi ficate Status Protocol (OCSP)
OCSP allows the A10 device to determine the revocation state of a submitted client certificate.
- The client sends a certi cate to the A10 device
- The A10 device checks the certi cate's validity
- The OCSP Responder returns the certi cate status (good, revoked, or unknown)
If the status is "good", the client is permitted to access the resources con figured on the server.
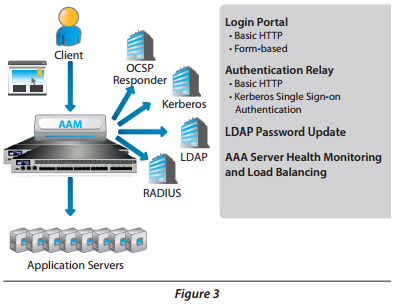
Sample Deployment
This diagram shows some of the available options when deploying AAM.
 |
 |
Summary
AAM o ffers a flexible choice of authentication schemes, seamless integration of authentication services, and enhanced security. A10 requires no licensing for AAM on A10 Thunder and AX Series ADCs, o ffering an exceptional value.

