
Web Application Firewall (WAF): Web Security Solution
 Web Application Level Security
Web Application Level Security
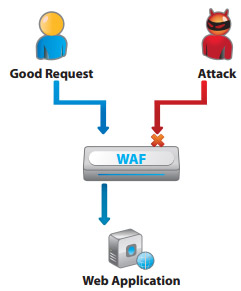
Applications that provide services to end-users can be vulnerable to many threats. Although many of these threats can be prevented by application developers, this often is outside the web site owner's control. A Web Application Firewall (WAF) provides a layer of control between end-users and applications.
A WAF filters all application access, inspecting both the tra ffic towards the web application and the response tra c from the application. By securing both the application infrastructure as well as the application user, a WAF complements traditional network firewalls, which are not designed to protect at this granular level.
Threat Vectors
Applications can be vulnerable to many threats that are not detected by regular network firewalls. The impact of these attacks can be quite severe. The Open Web Application Security Project (OWASP) has compiled a list of the top 10 risks that still threaten many web application deployments. The top 10 of 2010 is virtually identical to the new 2013 version; the most common attacks have not changed dramatically over the years. Here are some examples:
- Injection: SQL Injection Attacks use a Web form or other mechanism to send SQL commands or commands containing SQL special characters. By sending these SQL commands, the attacker can trigger the backend SQL database to execute the injected commands and allow unauthorized users to obtain sensitive information from the database.
- Cross-Site Scripting (XSS): XSS attacks exploit a Web server that does not validate data coming from another site. XSS can enable the attacker to obtain sensitive information, or to compromise a Web server.
- Sensitive Data Exposure: If Web applications do not protect sensitive data such as credit card numbers or Social Security Numbers (SSN), attackers are able to conduct identity theft, credit card fraud, or other crimes.
- Cross-Site Request Forgery (CSRF): CSRF attacks forge a user to send an HTTP request, including the victim's session cookie, to a vulnerable web application. To the vulnerable web application, this appears to be a legitimate request coming from the victim.
A10 WAF and Security
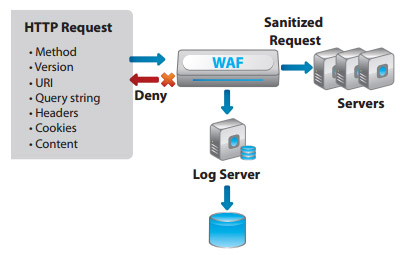
Available on its A10 Thunder or AX Series ADCs without license fees, A10's WAF module has many features to protect organizations from the most common attacks, protecting applications from malicious tra ffic.
The WAF enables a full defense stack with other A10 security mechanisms in order to protect web applications, ensure against code vulnerabilities and prevent data leakage; this aids in regulatory security compliance, such as Payment Card Industry (PCI) Data Security Standard (DSS) requirements.
A10's WAF feature is designed to recognize many of today's threats, with exibility to customize checks for emerging threats. The WAF is tightly integrated with other A10 security features within the Advanced Core Operating System (ACOS). Instead of integrating 3rd party WAF code, as many other vendors do, A10 has developed the WAF speci fically for ACOS. This approach results in a highly scalable and high performance security solution which is simple to con figure.
Attack Mitigation Examples
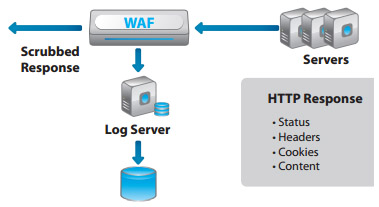
The WAF module o ffers granular control of Web application data flows. The WAF has various ways of dealing with threat vectors that can be launched at web applications.
Here are two use cases:
- The WAF can prevent bu er over ow attacks by setting accepted maximum thresholds for aspects of HTTP requests, and blocking requests that exceed the con gured limits.
- The WAF can strip HTTP response headers to "cloak" server information that can equip a hacker to target an attack on your Web servers. For example, the WAF can cloak an HTTP response header to hide the operating system that is running on your servers. Exposed HTTP headers can enable a hacker to more narrowly target your servers with attacks that are speci fic to the servers' operating systems.
The A10 WAF module o ffers many more features, including:
- Allowed HTTP keyword checks, such as GET, POST, and more
- SQL injection attack (SQLIA) check
- XSS check
- CSRF check
- Bad bot check
- Credit Card Number (CCN) masking
- Social Security Number (SSN) masking
- Perl Compatible Regular Expressions (PCRE) masking
- Cookie check
- Cookie encryption
- URI Black List/White List check
- HTTP protocol compliance check
- HTTP referer check
- Cloaking to hide server responses/error status codes
- Con gurable deny action
- Passive/Learning/Active deployment
- More…
Conclusion
With A10, organizations can attain peace of mind knowing their applications are protected from the most common attacks, especially those whose consequences can far exceed "common" consequences. A10 enables a full defense stack with WAF, DDoS protection, Application Access Management (AAM), SSL Intercept and more on its Thunder and AX Series appliances. All these features are designed for ACOS from the ground up and are fully integrated. A10 provides all these security features at no additional cost, as a single device solution.

